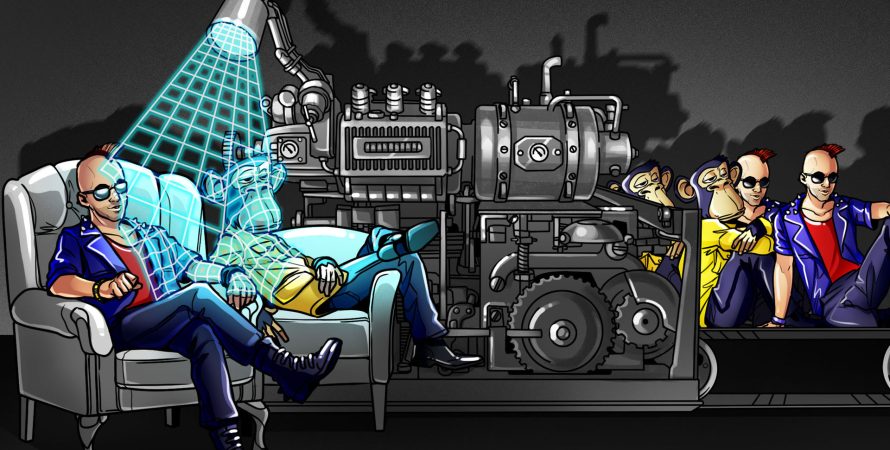
In the precariousness of Web3 open-source code, iterative development and “move fast” ethos, things break. And through breaking, things are also made. A new project allows anyone to create a copy of someone else’s NFT, aptly named “Mimics.”
But how does Mimics work, and what does it mean for the NFT art market to have a new variety of fakes? And will it result in token standards being upgraded and improved?
I met the anonymous founder of Mimics in a “Web3” office that was brimming with software developers writing lines of code as they nodded their heads in time to deep house and sipped cups of tea.
On semi-regular occasions, I drop in to visit some local devs in the blockchain space and learn more about what they are working on. They have always been welcoming and jovial, inviting me to share in their ritualistic Friday afternoon “meme creation hour” and have a go at spinning the in-office DJ decks.
They even offered me a desk to work from there for free, provided I clean the office once a week. I told them where to go (they were joking, but perhaps only half-joking as I stared at the overgrown vines living in the exposed beams in the roof).
It was at this office that I met the anon who would later take an extended sabbatical from their hand in engineering successful projects and, in their tinkering, discover and open-source a way to mimic your NFTs.
Stealing your NFTs
“I think I just broke the NFT market,” the anonymous founder told me flatly.
“Really? How?” I responded.
It turns out that art NFTs have a line of code in them called “tokenURI” or “URI” that acts like a pointer to the image being displayed. As the code is public, you can redirect your own NFT to make it look like anyone else’s. If you want your NFT to display a Cypherpunk, a Bored Ape, or how about a Pudgy Penguin? You got it.
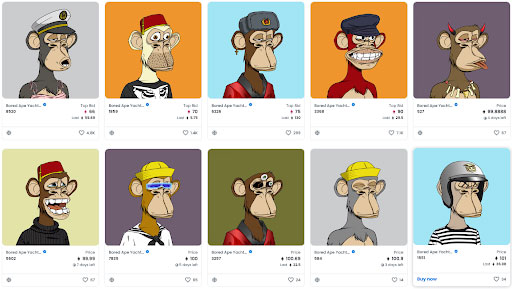
This means that your rare and expensive cartoon image NFT can essentially be cloned, not just by right-clicking copy-save as, and making another NFT of the same image but as a verifiable copy that has remnants of the real thing through code. Users rushing to clone a Bored Ape should beware, however:
“This could be a blatant breach of copyright or other IP,” states Australian crypto lawyer Joni Pirovich. “To determine rights that attach to the ownership of the token, and any image or metadata associated with the token, the buyer should try to identify whether any terms and conditions and any IP license applies to the ‘sale.’”
Many projects launch or resell on NFT marketplaces such as OpenSea without drafting their own terms or licenses and without revealing their identity. In these cases, they are not acting to protect any IP they own or allowing a person to understand who the copyright author may be and whether there is a human or computer that is generating the art and/or data. In Australia, copyright comes into existence when it is created by its author. In other countries, such as the United States, copyright is a registration system. NFTs (and associated metadata) are available globally and often without clear terms. This makes it unclear what IP laws apply.
Noticing that few others have cottoned on to the ramifications of how the NFT metadata works, the creator(s) of Mimics have open-sourced how to do it, of course.
Into the code
When it comes down to it, NFTs are really just tokens with a bundle of metadata. This data about data carries with it all the necessary information for someone else to locate and use it.
NFTs that can be mimicked via their metadata (so far) are ones that adhere to the most common ERC-721 and ERC-1155 standards.
ERC-721 and ERC-1155 standards provide two core sets of functionalities: controlling ownership of the token and getting data from the token. The latter function usually returns the appearance of an NFT to a website or wallet in order to display the NFT when “called” by a smart contract.
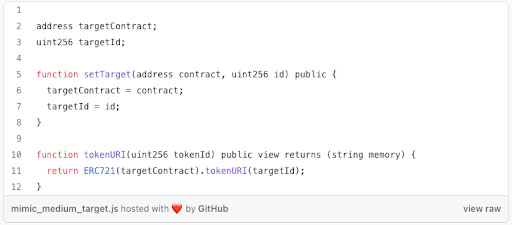
The trick with Mimics was realizing that the tokenURI can be called by a contract address. Particularly, it can be called inside the tokenURI function of another contract. Mimics hacks the metadata, allowing you to make an NFT that mimics the digital media attributes of another, such as an image or animation. Anyone anywhere can run this URI metadata function. Instead of the function being permissioned in the ERC standards so only the user can view an NFT or grant permissions to other sites to view it, it is public.
I ventured deeper into the Discord channel…
The Mimics project has open-sourced a codebase so you can mimic the “targetContract” and “targetId” of another NFT and make your NFT look just like that NFT.
“How about this cute jellyfish?” states the Mimicologists Guide docos.
On OpenSea, we can copy them from the page URL, the “Token Id” is the number on the far right, and the “Contract Address” is just to the left of it.
The Mimics contracts are now available. In true Web3 style, Mimics are permissionlessly available but technically a little tricky to access.
Initially, there was no web page front end, so you had to go on an “expedition” to interact directly with the “guild contract” on Etherscan. This was recently updated.
In a year that has seen some major heat in NFTs, how could Mimics affect markets? In the current context of market crashes, these lines of code and the token standards they draw upon have some serious implications for NFT owners, developers and the market at large.
What does this mean?
At this stage, Mimics don’t have implications for NFTs beyond artworks (such as copying NFTs with distinct functionalities to attest to membership). Only the metadata such as name, description, media and other attributes that are provided by the tokenURI can be mimicked. For something to be proxyable, it needs to be an attribute that an NFT provides on a public function or interface (meaning it is accessible by all users and other contracts on Ethereum) and not validated in any way by the website, service or contract receiving it.
Instead of being “law” to provably enforce the rules of the system, code here is the undermining factor in NFT security. Mimics prove the thesis by well-known cryptographer “Moxie” that crypto lacks cryptography in some respects — referring to cryptographically secure components of the codebase that make aspects of unique ownership provable, private and/or permissioned. Ironically, someone has already used the mimic contract to copy Moxie’s NFTs.
In some way, Mimics demonstrates a coordination failure in how open-source standards are made, peer-reviewed and adopted in Web3. This is until you see that Mimics actually forms part of the narrative of how these standards may evolve over time. Read More at COINTELEGRAPH![]()
Please Read Essential Disclaimer Information Here.
© 2024 Crypto Caster provides information. CryptoCaster.world does not provide investment advice. Do your research before taking a market position on the purchase of cryptocurrency and other asset classes. Past performance of any asset is not indicative of future results. All rights reserved.
Contribute to CryptoCaster℠ Via Metamask or favorite wallet. Send Coin/Token to Addresses Provided Below.
Thank you!
BTC – bc1qgdnd752esyl4jv6nhz3ypuzwa6wav9wuzaeg9g
ETH – 0x7D8D76E60bFF59c5295Aa1b39D651f6735D6413D
MATIC – 0x7D8D76E60bFF59c5295Aa1b39D651f6735D6413D
LITECOIN – ltc1qxsgp5fykl0007hnwgl93zr9vngwd2jxwlddvqt